

Imagine waking up to find your bank account drained, your personal photos circulating online, or your business brought to a standstill by hackers. These scenarios are not just scenes from a thriller—they’re real threats in today’s world. Cybersecurity has never been more critical, as our lives have become more interconnected and reliant on technology.
As technology advances, so do cybercriminals’ methods and tools. Their methods change at a pace that can be hard to keep up with. This underlines the importance of staying ahead of these emerging threats.
This post will shed light on some of the key cybersecurity threats that will emerge in the coming years. To help you, we’ll also provide insights into how you can shield yourself and your businesses from these threats.
Here are 6 emerging trends that will shape the cybersecurity space in the coming years and how you may adapt to them:
1. The Rise of AI-Powered Cybersecurity Attacks

Artificial Intelligence (AI) has brought many benefits, but it has also provided cyber criminals with powerful tools to improve their attacks. This has given rise to AI-powered cyber threats that are more sophisticated and a lot harder to detect than ever before.
How Do Cybercriminals Use AI?
Cybercriminals now use AI in several ways to carry out more effective attacks. AI algorithms can process vast amounts of data quickly, identify patterns, and adapt to changing conditions, making them ideal for automating and scaling up previously labour-intensive and time-consuming attacks.
Here are some common ways AI is being used by cybercriminals:
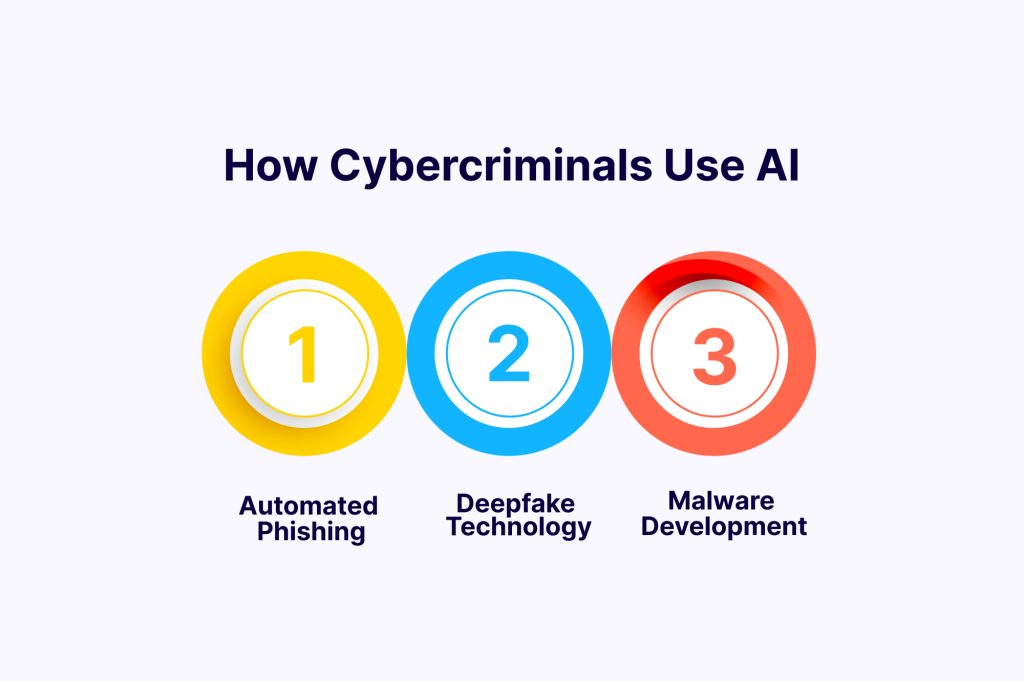
1. Automated Phishing: AI can generate highly personalised phishing emails by analysing social media profiles, previous communications, and other online footprints. This makes it much more likely that the target will fall for the scam.
2. Deepfake Technology: AI can create highly convincing fake audio and video recordings, known as deepfakes. These can be used to impersonate individuals and trick victims into divulging sensitive information or authorising fraudulent transactions.
3. Malware Development: AI can enhance malware by enabling it to learn from its environment, evade detection, and adapt its behaviour to overcome security measures.
Examples of AI-Powered Attacks
One alarming example of an AI-powered attack involves the use of deepfake technology. Imagine receiving a video call from someone who looks and sounds exactly like your CEO, instructing you to transfer funds to a new account. This actually happened.
The World Street Journal reports that criminals used deepfake audio to impersonate the CEO of a UK-based energy firm and successfully convinced an executive to transfer €220,000 to their account.
Automated phishing is another significant threat. Traditional phishing attacks involve sending out large volumes of generic emails, hoping that a few recipients will fall for the scam.
However, AI can craft emails designed for each recipient, making them much harder to spot.
What Are the Potential Impacts on Individuals and Businesses?
The consequences of AI-powered attacks can be severe. For individuals, these attacks can lead to identity theft, financial loss, and emotional distress. For businesses, the stakes are even higher. A successful AI-powered attack can result in significant financial losses, reputational damage, legal liabilities, and operational disruptions.
Imagine an AI-powered phishing attack targeting a company’s finance department. The attackers use personalised emails to trick employees into divulging login credentials for the company’s financial systems. Once inside, the attackers transfer large sums of money to their accounts, causing substantial financial damage to the company. Additionally, the company may face regulatory fines for failing to protect sensitive financial data.
How Can You Protect Against AI-Powered Threats?
Despite the sophisticated nature of AI-powered attacks, there are several strategies individuals and businesses can adopt to protect themselves:

1. Education and Training: Regularly educate employees about the latest phishing techniques and deepfake technology. Conduct training sessions that simulate these attacks to help employees recognise and respond to them appropriately.
2. Advanced Security Tools: Invest in AI-based security solutions that can detect and counteract AI-powered threats. These tools can analyse patterns and behaviours to identify potential threats that traditional security measures might miss.
3. Multi-Factor Authentication (MFA): Implement MFA for all sensitive accounts and systems. This adds an extra layer of security by requiring multiple forms of verification before granting access.
4. Regular Audits and Updates: Conduct regular security audits to identify vulnerabilities and ensure all software and systems are updated with the latest security patches.
5. Data Monitoring and Anomaly Detection: Use advanced monitoring tools to detect unusual activities in real-time. AI-based anomaly detection systems can identify deviations from normal patterns, indicating a potential security breach.
6. Strong Access Controls: Limit access to sensitive information and systems to only those who need it. Implement strict access controls and regularly review permissions.
If you stay informed about the latest AI developments and adopt these proactive measures, you and your business can significantly reduce the risk of falling victim to AI-powered attacks. As cybercriminals continue to change their tactics, vigilance and advanced security practices are needed to stay one step ahead.
2. Increased Sophistication in Phishing Schemes

Phishing attacks, once fairly basic, have become much more sophisticated and harder to detect. Cybercriminals constantly refine their tactics to make their emails and messages appear more legitimate, increasing the chances that their targets will fall for the scam.
Modern Phishing Tactics
In recent years, phishing schemes have evolved dramatically. Gone are the days of poorly written emails full of obvious errors. Today’s phishing attempts often involve highly convincing impersonations of trusted entities, such as banks, online services, or even colleagues.
Spear-phishing is one such tactic that has become increasingly common. Unlike traditional phishing, which involves sending out mass emails hoping a few recipients will fall for the scam, spear-phishing targets specific individuals within an organisation. Cybercriminals gather information from social media profiles, company websites, and other sources to craft personalised messages.
For example, a spear-phishing email might appear to come from a trusted coworker and include details about a recent project to make it seem more believable.
Another worthy of mention is whaling. Whaling is another tactic where attackers go after high-profile targets like executives. These attacks are particularly dangerous because executives often have access to sensitive information and funds.
What Are The Risks Associated with Phishing?
Let’s illustrate this using a scenario: A finance department employee might receive a spear-phishing email that looks like it’s from a supplier, urgently requesting an update to payment details. Believing the email to be legitimate, the employee changes the payment information, leading to large sums of money being transferred to the attackers’ accounts. This not only causes immediate financial loss but also damages the company’s reputation and can result in regulatory fines for failing to protect sensitive financial data.
How To Recognise and Avoid Phishing Attempts
Despite their increasing sophistication, there are ways to recognise and avoid phishing attempts. Here are some tips to help you stay safe:

1. Verify the Sender: Always check the sender’s email address carefully. Phishing emails often use addresses that are similar to legitimate ones but may have slight variations or misspellings.
2. Look for Red Flags: Be wary of emails that create a sense of urgency, pressure you to take immediate action, or ask for sensitive information. Phishing emails often try to provoke an emotional response to trick you into acting quickly without thinking.
3. Check Links Before Clicking: Hover over any links in the email to see the URL before clicking. If the URL looks suspicious or does not match the supposed sender’s domain, do not click on it.
4. Be Mindful of Unexpected Attachments: If you receive an unexpected attachment, especially from someone you don’t know, do not open it. Even if the email appears to be from a known contact, it’s wise to verify with the sender before opening any attachments.
5. Educate Yourself and Others: Regularly educate yourself and your colleagues about the latest phishing techniques. Many organisations offer training sessions that simulate phishing attacks to help employees recognise and avoid them.
6. Use Security Software: Invest in robust security software with features like email filtering, malware detection, and anti-phishing tools. These can help identify and block phishing attempts before they reach your inbox.
Remember, a healthy dose of scepticism and a few extra seconds of scrutiny can go a long way in protecting yourself and your organisation from cyber threats.
3. The Growing Ransomware Cybersecurity Threat

Ransomware is a type of malware that encrypts a victim’s files, with the attacker demanding a ransom to restore access. Over the past few years, ransomware attacks have become more frequent and more damaging. High-profile attacks on large companies and public institutions have made headlines, but smaller businesses and individuals are also at risk.
The Rise of Ransomware
Ransomware has been around for a while, but its prevalence has surged in recent years. Attackers have become more skilled at spreading this malware, and the potential profits have driven them to launch more attacks. One of the most infamous ransomware attacks was WannaCry in 2017, which affected hundreds of thousands of computers across the globe, including systems within the UK’s National Health Service. This attack caused widespread disruption and exposed the devastating potential of ransomware.
Notable Ransomware Attacks
Several notable ransomware attacks have demonstrated the severity of this threat. The WannaCry attack, mentioned earlier, is one such example. Another significant incident was the attack on Colonial Pipeline in 2021, which led to fuel shortages across the southeastern United States. The attackers demanded a ransom to restore operations, and the company eventually paid nearly $5 million to regain control of their systems.
These incidents demonstrate how ransomware can cripple essential services and infrastructure, leading to significant economic and societal damage. They also show that even well-prepared organisations can fall victim to these attacks, it highlights the need for more robust security measures.
Evolution of Ransomware Techniques
Ransomware techniques have evolved significantly. Early ransomware attacks typically relied on users downloading malicious attachments from spam emails. However, attackers have developed more sophisticated methods to spread their malware and increase their chances of success.
One of the newer techniques is “double extortion.” In this method, attackers not only encrypt the victim’s files but they also steal sensitive data. They then threaten to release this data publicly if the ransom is not paid. This pressure often compels victims to pay the ransom.
Another technique involves targeting managed service providers (MSPs). By compromising an MSP, attackers can gain access to multiple clients’ networks, thereby amplifying the impact of their attack and increasing the likelihood of a significant payout.
How Can You Prevent and Respond to Ransomware Attacks?
Preventing ransomware requires a combination of proactive measures and effective response strategies. Here are some best practices for reducing the risk of a ransomware attack and minimising damage if one occurs:
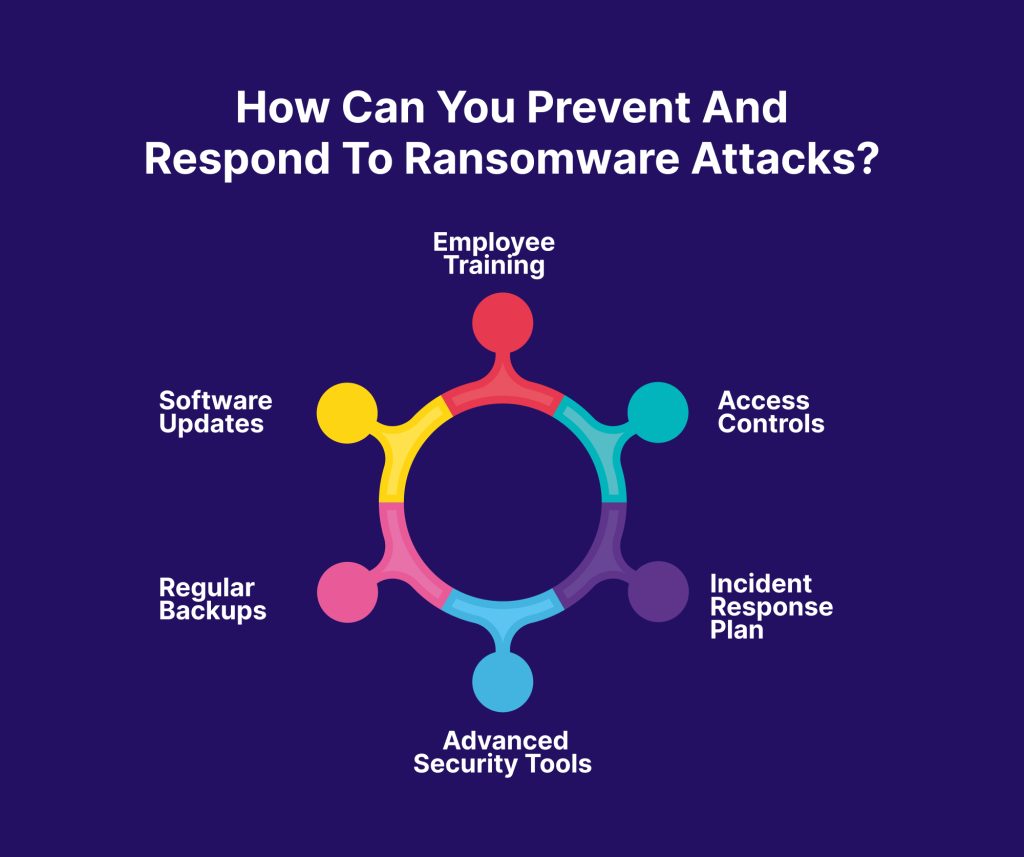
1. Regular Backups: Regularly back up your data and ensure that backups are stored securely and offline. This allows you to restore your data without paying the ransom if an attack occurs.
2. Software Updates: Keep your operating systems, software, and antivirus programs up to date with the latest patches and updates. This can help close security vulnerabilities that ransomware can exploit.
3. Employee Training: Educate employees about the risks of ransomware and how to recognise potential threats. This includes being cautious with email attachments, avoiding suspicious links, and reporting any unusual activity.
4. Access Controls: Implement strong access controls to limit the spread of ransomware if it does infiltrate your network. This includes using multi-factor authentication and restricting user permissions to only what is necessary for their role.
5. Incident Response Plan: Develop and regularly update an incident response plan that outlines the steps to take if a ransomware attack occurs. This plan should include procedures for isolating infected systems, communicating with stakeholders, and restoring data from backups.
6. Advanced Security Tools: Use advanced security tools, such as intrusion detection systems and endpoint protection, to detect and block ransomware before it can cause damage. These tools can help identify unusual activity and stop attacks in their tracks.
Ransomware is a growing threat, but by implementing strong security practices, you can protect yourself and your organisation from its devastating effects. Regularly updating your defences and preparing for potential attacks will help you stay one step ahead of cybercriminals.
4. Cybersecurity Attacks on Supply Chain Systems

Supply chain attacks have emerged as a significant cybersecurity threat that poses serious risks to businesses and consumers alike. These attacks target the interconnected network of suppliers and vendors that organisations rely on, exploiting vulnerabilities to infiltrate their systems and compromise sensitive data.
Understanding Supply Chain Attacks
Supply chain attacks involve targeting the weakest link in a company’s network—the suppliers and vendors that provide goods and services. By compromising these third-party entities, attackers can gain access to the networks and systems of their customers, often with devastating consequences. These attacks can take various forms, including malware insertion, data breaches, and software supply chain compromise.
Notable Examples of Supply Chain Attacks
The UK has experienced its fair share of supply chain attacks, with several high-profile incidents highlighting the severity of this threat. One notable example is the SolarWinds attack, which affected numerous government agencies and private sector organisations worldwide. While the direct impact on UK businesses may not have been as pronounced as in other countries, the incident underscored the global reach and sophistication of supply chain attacks.
Another significant attack targeted the software vendor Codecov, which provides code testing services to thousands of organisations, including many in the UK. Hackers exploited a vulnerability in Codecov’s systems to gain unauthorised access to customer networks, potentially compromising sensitive data and intellectual property.
What is the Impact on Businesses and Consumers?
The impact of supply chain attacks can be far-reaching, affecting not only the targeted organisations but also their customers and partners.
In the SolarWinds attack, the compromised software was used by numerous government agencies and critical infrastructure providers, raising concerns about the security of national systems and infrastructure. The incident also highlighted the need for greater transparency and accountability in the software supply chain and improved cybersecurity measures to detect and mitigate such attacks.
How To Control Supply Chain Risks
Mitigating the risks associated with supply chain attacks requires a multi-faceted approach. Here are some strategies for protecting against supply chain attacks:
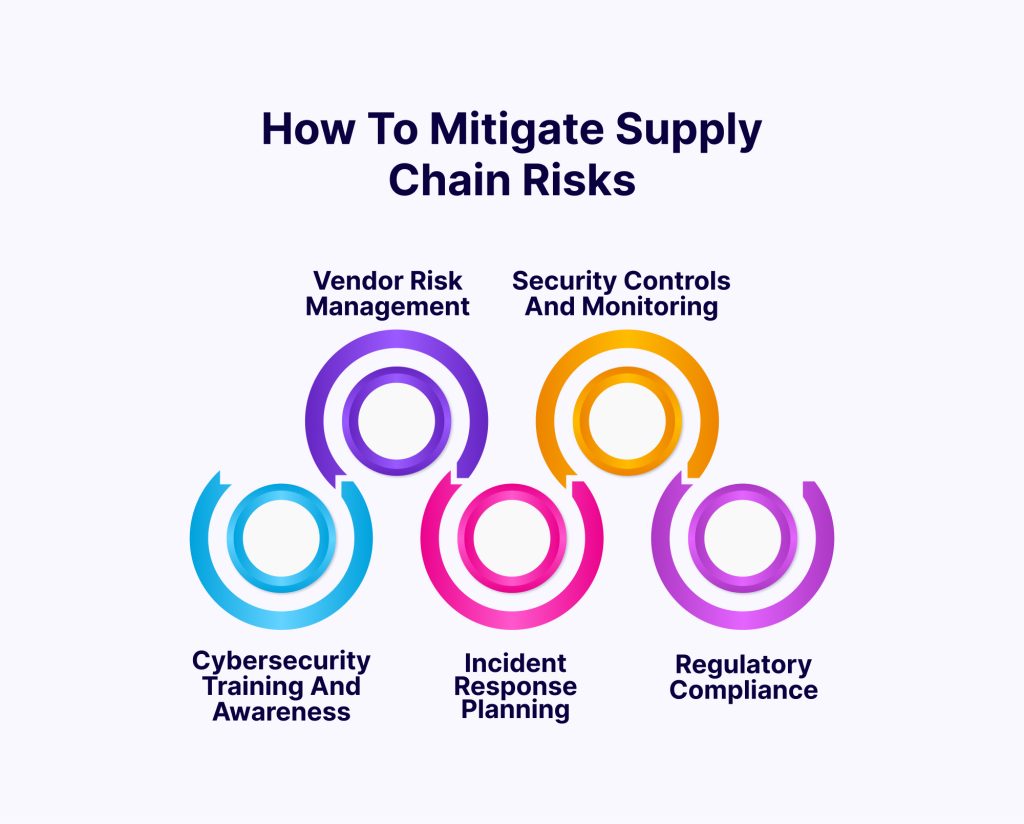
1. Vendor Risk Management: Implement robust vendor risk management processes to assess the security posture of third-party suppliers and vendors. This includes conducting due diligence assessments, monitoring vendor security practices, and requiring adherence to cybersecurity standards and best practices.
2. Security Controls and Monitoring: Implement security controls and monitoring mechanisms to detect and respond to suspicious activity within your supply chain. This may include network segmentation, intrusion detection systems, and real-time threat intelligence monitoring.
3. Cybersecurity Training and Awareness: Provide cybersecurity training and awareness programmes for employees, vendors, and partners to educate them about the risks of supply chain attacks and how to identify and report suspicious activity.
4. Incident Response Planning: Develop and regularly test incident response plans that outline the steps to take during a supply chain attack. This includes establishing clear communication channels, coordinating response efforts with relevant stakeholders, and preserving evidence for forensic analysis.
5. Regulatory Compliance: Stay informed about relevant regulations and compliance requirements related to supply chain security, such as the GDPR and ISO 27001. Ensure that your organisation complies with these standards and maintains appropriate safeguards to protect sensitive data.
By proactively addressing supply chain risks and implementing robust cybersecurity measures, businesses can strengthen their resilience to supply chain attacks and better protect their customers, partners, and stakeholders.
While supply chain attacks may continue to evolve and pose new challenges, a proactive and collaborative approach to cybersecurity can help mitigate the risks and ensure the integrity and security of the supply chain ecosystem.
5. Cybersecurity for Internet of Things (IoT) Devices: Protecting Our Connected World

The Internet of Things (IoT) has transformed how we interact with technology; it seamlessly integrates internet-connected devices into our daily lives. From smart thermostats and wearable fitness trackers to connected kitchen appliances and industrial sensors, IoT devices offer convenience, efficiency, and new capabilities. However, this popularity of IoT devices also brings significant security challenges that must be addressed to protect our privacy, safety, and digital assets.
Understanding IoT and Its Impact
The Internet of Things refers to a network of interconnected devices embedded with sensors, software, and other technologies that enable them to collect and exchange data. These devices can communicate with each other, share data with cloud services, and be remotely controlled via smartphone apps or web interfaces. The potential applications of IoT are vast, spanning various industries, including healthcare, transportation, agriculture, and manufacturing.
The integration of IoT devices into our daily lives has impacted many aspects of how we live, work, and interact with our environment. Smart home devices, for example, allow homeowners to remotely control lighting, heating, and security systems, enhancing convenience and energy efficiency.
In healthcare, wearable devices can monitor vital signs, track physical activity, and provide real-time health data to patients and healthcare providers, enabling more personalised and proactive healthcare management.
Security Challenges of IoT Devices
Despite their numerous benefits, IoT devices also present significant security challenges that can be exploited by malicious actors. Many IoT devices are designed with convenience and functionality in mind, prioritising ease of use and connectivity over security. As a result, they often lack basic security features, such as encryption, secure authentication mechanisms, and regular software updates. This makes them vulnerable to various cyber threats, including:
1. Unauthorised Access: Weak or default passwords, unencrypted communication channels, and insecure authentication mechanisms make IoT devices susceptible to unauthorised access by hackers. Once compromised, these devices can be used to launch further attacks or spy on users.
2. Data Privacy Risks: IoT devices collect vast amounts of sensitive data, including personal information, location data, and behavioural patterns. Inadequate data encryption and insecure data storage practices can expose this information to unauthorised access or interception, leading to privacy violations and identity theft.
3. Device Tampering and Manipulation: Hackers can exploit vulnerabilities in IoT devices to tamper with their functionality, manipulate sensor readings, or remotely control them for malicious purposes. This poses risks to user safety, property security, and the integrity of critical systems.
4. Botnet Attacks: IoT devices are increasingly being recruited into botnets—networks of compromised devices controlled by cybercriminals for various malicious activities, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and cryptocurrency mining.
Examples of IoT Vulnerabilities and Breaches
Numerous real-world examples highlight the severity of IoT security vulnerabilities and their potential impact on individuals, businesses, and society at large. In 2016, the Mirai botnet exploited insecure IoT devices, such as internet-connected cameras and routers, to launch massive DDoS attacks that disrupted major internet services worldwide. The attack underscored the risks of unsecured IoT devices and the importance of securing them against exploitation.
Researchers have also shown how vulnerabilities in smart home devices could be exploited to gain unauthorised access to users’ homes. By exploiting weaknesses in smart locks, security cameras, and other IoT devices, attackers could bypass physical security measures and remotely control home automation systems, posing risks to occupants’ safety and property security.
How to Secure IoT Devices: Best Practices and Recommendations
Securing IoT devices requires a proactive and multi-layered approach that addresses both technical and organisational aspects of cybersecurity. Here are some best practices and recommendations for improving the security of IoT devices:
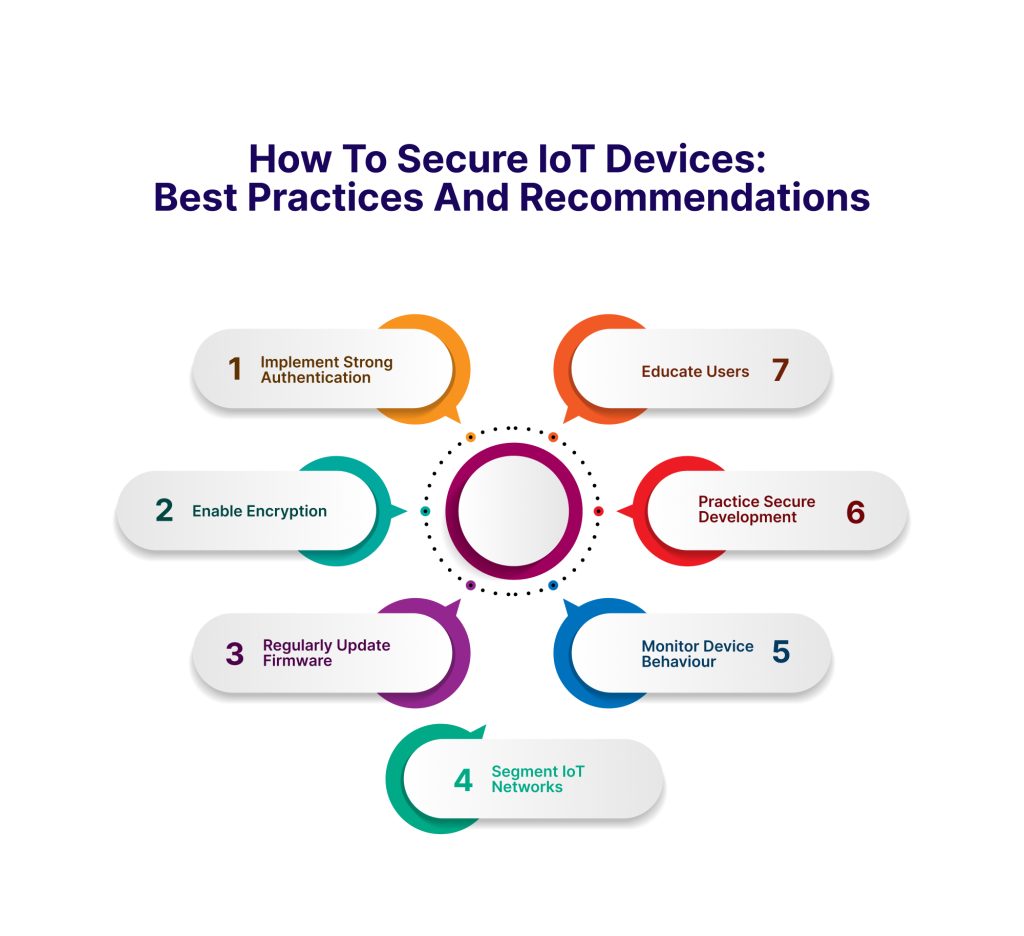
1. Implement Strong Authentication: Use strong, unique passwords for IoT devices and change default credentials to prevent unauthorised access. Enable multi-factor authentication (MFA) where possible to add an extra layer of security.
2. Enable Encryption: Encrypt data both in transit and at rest to protect it from interception and unauthorised access. Use industry-standard encryption protocols and algorithms to secure communication channels and storage systems.
3. Regularly Update Firmware: Keep IoT device firmware and software up to date with the latest security patches and updates. Manufacturers should provide timely security patches and release updates to address known vulnerabilities and improve device security.
4. Segment IoT Networks: Separate IoT devices from critical network infrastructure and sensitive data to minimise the impact of a potential compromise. Use network segmentation and access controls to isolate IoT devices and restrict their communication to necessary services and resources.
5. Monitor Device Behaviour: Implement monitoring and anomaly detection systems to identify suspicious activity and potential security incidents involving IoT devices. Monitor network traffic, device logs, and behaviour patterns to detect signs of unauthorised access, data exfiltration, or device tampering.
6. Practice Secure Development: Follow secure coding practices and design principles when developing IoT devices and software. Conduct thorough security assessments, penetration testing, and code reviews to identify and mitigate potential security vulnerabilities early in the development lifecycle.
7. Educate Users: Provide comprehensive security awareness training for IoT device users to educate them about potential risks, best practices, and security hygiene. Encourage users to update firmware regularly, use strong passwords, and report any suspicious activity or security incidents promptly.
Securing IoT devices is essential to safeguarding privacy, protecting critical infrastructure, and maintaining trust and confidence in the IoT ecosystem. As the adoption of IoT continues to grow, prioritising security and resilience will be crucial to realising the full potential of connected technologies while minimising associated risks.
6. Cloud Security Challenges

The rapid adoption of cloud services has transformed the way businesses operate, offering flexibility, scalability, and cost savings. However, along with these benefits come significant security challenges that organisations must address to protect their data and assets in the cloud.
The Rise of Cloud Services
Cloud computing has become very popular today, with businesses of all sizes leveraging cloud platforms for storage, computing power, and software-as-a-service (SaaS) applications. From startups to multinational corporations, the cloud offers unparalleled flexibility and agility, allowing organisations to innovate and scale their operations rapidly.
Common Cloud Security Concerns
Despite the benefits of cloud computing, security remains a top concern for businesses migrating to the cloud. Data breaches, misconfigurations, and insider threats are among the most pressing security challenges organisations face in the cloud.
Data breaches are a significant concern, with cybercriminals constantly targeting cloud environments to steal sensitive information or disrupt operations. Misconfigurations, such as improperly configured storage buckets or access control policies, can expose sensitive data to unauthorised access or accidental disclosure. Insider threats, whether intentional or unintentional, pose additional risks, highlighting the importance of robust access controls and monitoring mechanisms.
Examples of Cloud Security Incidents
Numerous high-profile cloud security incidents have underscored the severity of these risks. One notable example is the Capital One data breach in 2019, where a misconfigured web application firewall led to the exposure of over 100 million customer records stored in Amazon Web Services (AWS) S3 buckets.
Another incident involved the compromise of Docker Hub repositories, resulting in the unauthorised access and modification of container images used by thousands of organisations worldwide.
Best Practices for Securing Cloud Environments
Securing cloud environments requires a proactive and multi-layered approach that addresses both technical and organisational aspects of cybersecurity. Here are some best practices for protecting data and assets in the cloud:
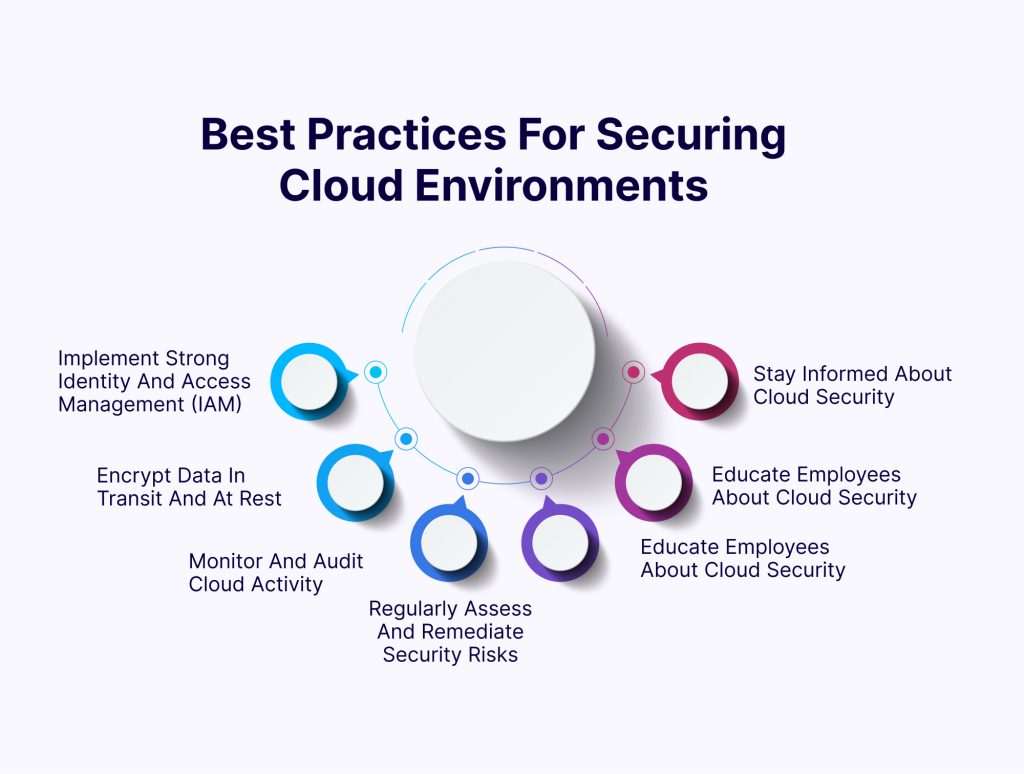
1. Implement Strong Identity and Access Management (IAM): Use robust IAM controls to manage user access and permissions effectively. Implement multi-factor authentication (MFA), least privilege principles, and regular access reviews to prevent unauthorised access.
2. Encrypt Data in Transit and at Rest: Use encryption to protect data both in transit and at rest. Leverage encryption mechanisms provided by cloud service providers, such as AWS Key Management Service (KMS) or Azure Key Vault, to safeguard sensitive information from unauthorised access.
3. Monitor and Audit Cloud Activity: Implement comprehensive logging and monitoring capabilities to track user activity, detect suspicious behaviour, and respond to security incidents promptly. Use cloud-native monitoring tools and third-party solutions to gain visibility into cloud environments and identify potential security threats.
4. Regularly Assess and Remediate Security Risks: Conduct regular security assessments, vulnerability scans, and penetration tests to identify and remediate security risks in cloud environments. Address misconfigurations, software vulnerabilities, and other security issues promptly to reduce the likelihood of a breach.
5. Educate Employees About Cloud Security: Provide ongoing training and awareness programs to educate employees about the importance of cloud security and their role in protecting data and assets. Promote security best practices, such as strong password management, data classification, and secure coding principles.
Stay Informed About Cloud Security Threats: Stay informed about the latest cloud security threats, trends, and best practices through industry publications, security blogs, and professional networks. Participate in cloud security communities and forums to share knowledge and learn from others’ experiences.
While cloud security challenges may continue to evolve, a proactive and holistic approach to cybersecurity is essential to safeguarding sensitive information and maintaining trust in cloud services.
Final Thoughts
As we adapt to the realities of our new digital environment, education and collaboration will be our most potent weapons against cyber threats. We can protect ourselves and our digital assets from harm by continuing to learn, adapt, and implement effective cyber security measures.
Furthermore, choosing a trusted internet services provider like Docalla can significantly enhance your cyber security posture. Docalla is committed to delivering not only fast and reliable broadband but also implementing advanced security protocols to safeguard your online activities and data.
In conclusion, the journey towards cyber security is ongoing and dynamic. Let’s commit to staying informed, remaining vigilant, and working together to safeguard our digital future. With partners like Docalla by your side, you can navigate the digital world with greater confidence and peace of mind. Together, we can build a safer and more secure online environment for all.